###########################################################
testssl.sh 2.8rc2 from https://testssl.sh/dev/
(d32dbda 2016-10-12 21:15:37 -- 1.558)
This program is free software. Distribution and
modification under GPLv2 permitted.
USAGE w/o ANY WARRANTY. USE IT AT YOUR OWN RISK!
Please file bugs @ https://testssl.sh/bugs/
###########################################################
Start 2016-11-07 16:39:33 -->> 85.17.82.133:443 (bluelight.org) <<--
rDNS (85.17.82.133): bluelight.org.
Service detected: HTTP
Testing protocols (via sockets except TLS 1.2, SPDY+HTTP2)
SSLv2 not offered (OK)
SSLv3 not offered (OK)
TLS 1 offered
TLS 1.1 offered
TLS 1.2 offered (OK)
Version tolerance downgraded to TLSv1.2 (OK)
SPDY/NPN not offered
HTTP2/ALPN http/1.1 (offered)
Testing ~standard cipher lists
Null Ciphers not offered (OK)
Anonymous NULL Ciphers not offered (OK)
Anonymous DH Ciphers not offered (OK)
40 Bit encryption not offered (OK)
56 Bit encryption not offered (OK)
Export Ciphers (general) not offered (OK)
Low (<=64 Bit) not offered (OK)
DES Ciphers not offered (OK)
"Medium" grade encryption not offered (OK)
Triple DES Ciphers offered
High grade encryption offered (OK)
Testing robust (perfect) forward secrecy, (P)FS -- omitting Null Authentication/Encryption as well as 3DES an
PFS is offered (OK) DHE-RSA-AES128-GCM-SHA256 DHE-RSA-AES128-SHA256 DHE-RSA-AES128-SHA DHE-RSA-AES25 ECDHE-RSA-AES128-GCM-SHA256 ECDHE-RSA-AES128-SHA256 ECDHE-RSA-AES128-SHA ECDHE-RSA-AES256-GCM-SHA384 ECDHE-RS
Elliptic curves offered: sect571r1 sect571k1 sect409k1 sect409r1 sect283k1 sect283r1 prime256v1 secp521r1
Testing server preferences
Has server cipher order? yes (OK)
Negotiated protocol TLSv1.2
Negotiated cipher ECDHE-RSA-AES128-GCM-SHA256, 256 bit ECDH
Cipher order
TLSv1: ECDHE-RSA-AES128-SHA ECDHE-RSA-AES256-SHA DHE-RSA-AES128-SHA DHE-RSA-AES256-SHA AES128-SHA AES2
TLSv1.1: ECDHE-RSA-AES128-SHA ECDHE-RSA-AES256-SHA DHE-RSA-AES128-SHA DHE-RSA-AES256-SHA AES128-SHA AES2
TLSv1.2: ECDHE-RSA-AES128-GCM-SHA256 ECDHE-RSA-AES256-GCM-SHA384 DHE-RSA-AES128-GCM-SHA256 DHE-RSA-AES25A DHE-RSA-AES128-SHA256 DHE-RSA-AES128-SHA DHE-RSA-AES256-SHA256 DHE-RSA-AES256-SHA AES128-GCM-SHA256 AES256-GHE-RSA-CAMELLIA128-SHA CAMELLIA128-SHA DES-CBC3-SHA
Testing server defaults (Server Hello)
TLS extensions (standard) "server name/#0" "renegotiation info/#65281" "EC point formats/#11" "session tic
Session Tickets RFC 5077 300 seconds (PFS requires session ticket keys to be rotated <= daily)
SSL Session ID support yes
TLS clock skew random values, no fingerprinting possible
Signature Algorithm SHA256 with RSA
Server key size RSA 2048 bits
Fingerprint / Serial SHA1 A92E6694C7B511A7895AC9D7756ECB03B695DF08 / B06F8810195A3CBC087F8BA45B0D57D1
SHA256 085ED2B235272F7643CE0CC541E35E46BB3BC6DCDCDFCC7E51237AFC4298DCF8
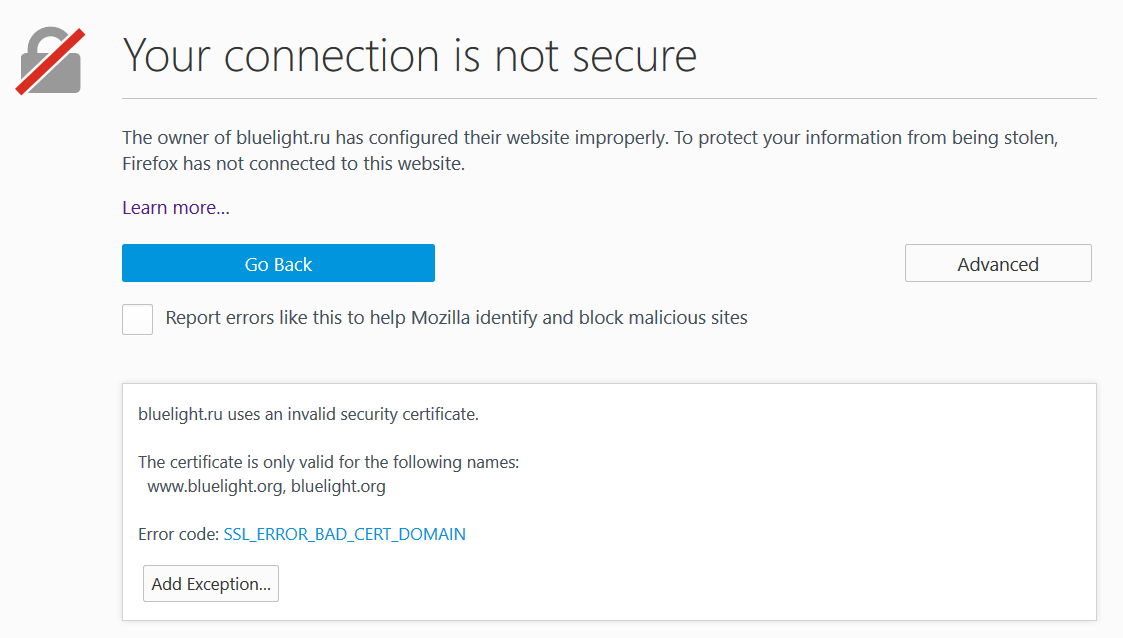
Common Name (CN) "www.bluelight.org"
subjectAltName (SAN) "www.bluelight.org" "bluelight.org"
Issuer "COMODO RSA Domain Validation Secure Server CA" ("COMODO CA Limited" from "GB")
Trust (hostname) Ok via SAN (works w/o SNI)
Chain of trust Ok
EV cert (experimental) no
Certificate Expiration 818 >= 60 days (2014-02-03 19:00 --> 2019-02-03 18:59 -0500)
# of certificates provided 4
Certificate Revocation List http://crl.comodoca.com/COMODORSADomainValidationSecureServerCA.crl
OCSP URI http://ocsp.comodoca.com
OCSP stapling offered
Testing HTTP header response @ "/"
HTTP Status Code 302 Found, redirecting to "/vb/content.php"
HTTP clock skew 0 sec from localtime
Strict Transport Security --
Public Key Pinning --
Server banner Apache
Application banner --
Cookie(s) (none issued at "/") -- maybe better try target URL of 30x
Security headers --
Reverse Proxy banner --
Testing vulnerabilities
Heartbleed (CVE-2014-0160) not vulnerable (OK), timed out
CCS (CVE-2014-0224) not vulnerable (OK)
Secure Renegotiation (CVE-2009-3555) not vulnerable (OK)
Secure Client-Initiated Renegotiation not vulnerable (OK)
CRIME, TLS (CVE-2012-4929) not vulnerable (OK)
BREACH (CVE-2013-3587) no HTTP compression (OK) - only supplied "/" tested
POODLE, SSL (CVE-2014-3566) not vulnerable (OK)
TLS_FALLBACK_SCSV (RFC 7507), Downgrade attack prevention supported (OK)
FREAK (CVE-2015-0204) not vulnerable (OK)
DROWN (2016-0800, CVE-2016-0703) not vulnerable on this port (OK)
make sure you don't use this certificate elsewhere with SSLv2 enabl
https://censys.io/ipv4?q=085ED2B235272F7643CE0CC541E35E46BB3BC6DCDC
LOGJAM (CVE-2015-4000), experimental not vulnerable (OK), common primes not checked. See below for any D
BEAST (CVE-2011-3389) TLS1: DES-CBC3-SHA AES128-SHA
DHE-RSA-AES128-SHA AES256-SHA DHE-RSA-AES256-SHA
CAMELLIA128-SHA DHE-RSA-CAMELLIA128-SHA CAMELLIA256-SHA
DHE-RSA-CAMELLIA256-SHA ECDHE-RSA-AES128-SHA ECDHE-RSA-AES256
VULNERABLE -- but also supports higher protocols (possible mitigati
RC4 (CVE-2013-2566, CVE-2015-2808) no RC4 ciphers detected (OK)
Testing all 183 locally available ciphers against the server, ordered by encryption strength
Hexcode Cipher Suite Name (OpenSSL) KeyExch. Encryption Bits Cipher Suite Name (RFC)
--------------------------------------------------------------------------------------------------------------
xc030 ECDHE-RSA-AES256-GCM-SHA384 ECDH 256 AESGCM 256 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
xc028 ECDHE-RSA-AES256-SHA384 ECDH 256 AES 256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
xc014 ECDHE-RSA-AES256-SHA ECDH 256 AES 256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
x9f DHE-RSA-AES256-GCM-SHA384 DH 2048 AESGCM 256 TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
x6b DHE-RSA-AES256-SHA256 DH 2048 AES 256 TLS_DHE_RSA_WITH_AES_256_CBC_SHA256
x39 DHE-RSA-AES256-SHA DH 2048 AES 256 TLS_DHE_RSA_WITH_AES_256_CBC_SHA
x88 DHE-RSA-CAMELLIA256-SHA DH 2048 Camellia 256 TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA
x9d AES256-GCM-SHA384 RSA AESGCM 256 TLS_RSA_WITH_AES_256_GCM_SHA384
x3d AES256-SHA256 RSA AES 256 TLS_RSA_WITH_AES_256_CBC_SHA256
x35 AES256-SHA RSA AES 256 TLS_RSA_WITH_AES_256_CBC_SHA
x84 CAMELLIA256-SHA RSA Camellia 256 TLS_RSA_WITH_CAMELLIA_256_CBC_SHA
xc02f ECDHE-RSA-AES128-GCM-SHA256 ECDH 256 AESGCM 128 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
xc027 ECDHE-RSA-AES128-SHA256 ECDH 256 AES 128 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
xc013 ECDHE-RSA-AES128-SHA ECDH 256 AES 128 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
x9e DHE-RSA-AES128-GCM-SHA256 DH 2048 AESGCM 128 TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
x67 DHE-RSA-AES128-SHA256 DH 2048 AES 128 TLS_DHE_RSA_WITH_AES_128_CBC_SHA256
x33 DHE-RSA-AES128-SHA DH 2048 AES 128 TLS_DHE_RSA_WITH_AES_128_CBC_SHA
x45 DHE-RSA-CAMELLIA128-SHA DH 2048 Camellia 128 TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA
x9c AES128-GCM-SHA256 RSA AESGCM 128 TLS_RSA_WITH_AES_128_GCM_SHA256
x3c AES128-SHA256 RSA AES 128 TLS_RSA_WITH_AES_128_CBC_SHA256
x2f AES128-SHA RSA AES 128 TLS_RSA_WITH_AES_128_CBC_SHA
x41 CAMELLIA128-SHA RSA Camellia 128 TLS_RSA_WITH_CAMELLIA_128_CBC_SHA
x0a DES-CBC3-SHA RSA 3DES 168 TLS_RSA_WITH_3DES_EDE_CBC_SHA
Running browser simulations via sockets (experimental)
Android 2.3.7 TLSv1.0 DHE-RSA-AES128-SHA
Android 4.0.4 TLSv1.0 ECDHE-RSA-AES128-SHA
Android 4.1.1 TLSv1.0 ECDHE-RSA-AES128-SHA
Android 4.2.2 TLSv1.0 ECDHE-RSA-AES128-SHA
Android 4.3 TLSv1.0 ECDHE-RSA-AES128-SHA
Android 4.4.2 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256
Android 5.0.0 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256
Baidu Jan 2015 TLSv1.0 ECDHE-RSA-AES128-SHA
BingPreview Jan 2015 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256
Chrome 47 / OSX TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256
Firefox 31.3.0ESR / Win7 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256
Firefox 42 OS X TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256
GoogleBot Feb 2015 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256
IE 6 XP No connection
IE 7 Vista TLSv1.0 ECDHE-RSA-AES128-SHA
IE 8 XP TLSv1.0 DES-CBC3-SHA
IE 8-10 Win 7 TLSv1.0 ECDHE-RSA-AES128-SHA
IE 11 Win 7 TLSv1.2 DHE-RSA-AES128-GCM-SHA256
IE 11 Win 8.1 TLSv1.2 ECDHE-RSA-AES128-SHA256
IE 10 Win Phone 8.0 TLSv1.0 ECDHE-RSA-AES128-SHA
IE 11 Win Phone 8.1 TLSv1.2 ECDHE-RSA-AES128-SHA256
IE 11 Win Phone 8.1 Update TLSv1.2 DHE-RSA-AES128-GCM-SHA256
IE 11 Win 10 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256
Edge 13 Win 10 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256
Edge 13 Win Phone 10 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256
Java 6u45 TLSv1.0 DHE-RSA-AES128-SHA
Java 7u25 TLSv1.0 ECDHE-RSA-AES128-SHA
Java 8u31 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256
OpenSSL 0.9.8y TLSv1.0 DHE-RSA-AES128-SHA
OpenSSL 1.0.1l TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256
OpenSSL 1.0.2e TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256
Safari 5.1.9 OS X 10.6.8 TLSv1.0 ECDHE-RSA-AES128-SHA
Safari 6 iOS 6.0.1 TLSv1.2 ECDHE-RSA-AES128-SHA256
Safari 6.0.4 OS X 10.8.4 TLSv1.0 ECDHE-RSA-AES128-SHA
Safari 7 iOS 7.1 TLSv1.2 ECDHE-RSA-AES128-SHA256
Safari 7 OS X 10.9 TLSv1.2 ECDHE-RSA-AES128-SHA256
Safari 8 iOS 8.4 TLSv1.2 ECDHE-RSA-AES128-SHA256
Safari 8 OS X 10.10 TLSv1.2 ECDHE-RSA-AES128-SHA256
Safari 9 iOS 9 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256
Safari 9 OS X 10.11 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256
Done 2016-11-07 16:42:49 -->> 85.17.82.133:443 (bluelight.org) <<--